The Engineering Logic Behind The New Tria Login Security Protocol Morra Joins Nerej
Tria adopts a novel approach to public key cryptography by leveraging threshold signature schemes (tss) Two central results for pcl are a set of composition theorems and a computational soundness theorem Tss facilitates asynchronous decentralized key generation (adkg) and signatures, departing from the traditional public key infrastructure (pki) reliant on centralized key custodians.
Network access layer security protocol | PDF
However, the complexity of these protocols makes them vulnerable to various security threats. Protocol composition logic (pcl) summary pcl is a logic for proving security properties of network protocols Our audit provides a security assessment based on the best industry practices at the time of review, identifying known vulnerabilities in the submitted smart contract source code, including its compilation, deployment, and intended functionality.
- The Great Debate Parents React To Saint Paul Schools 2026 Homework Policy Shift
- Inside The Sustainable Land Management Techniques Of Branch Kampe
- Sustainable Cities And Green Tech Building A Resilient Future Society
While the industry debates whether to trust validators, oracles, or governance tokens, trinity protocol eliminates trust entirely through mathematical certainty across three independent.
Cryptography and network security are essential for protecting information systems from unauthorized access, ensuring secure communication, and maintaining trust in today's digital world. Tria specializes in designing and building full hmi (human machine interface) solutions for oems that need compute, display and controls all in one unit Built to operate in the most challenging environments. A tap, a password, a face scan, and boom, you're in
But behind that simple act There's a whole world of authentication protocols working hard to keep things secure. The new secure data communications protocol uses the internet protocol and it standards for security (tls 1.3) and communicates securely across firewalls and the public internet. Multidimensional security protocol engineering is effective for creating cryptographic protocols since it encompasses a variety of design, analysis, and deployment techniques, thereby providing a higher level of confidence than individual approaches offer

Spear ii, the security protocol engineering and analysis resource ii, is a protocol engineering tool built on the foundation of previous.
Match the type of attack with its description or example • question theft of trade secrets social engineering logic bombs an employee rigs the accounting system to make improper periodic payments and hides them from auditors. For developers, understanding these protocols is crucial because they influence how websites are built, how data is transferred, and how user security is handled Whether you're creating login systems, fetching data from a server, or ensuring fast page loads, web protocols ensure your application works smoothly, securely, and efficiently.
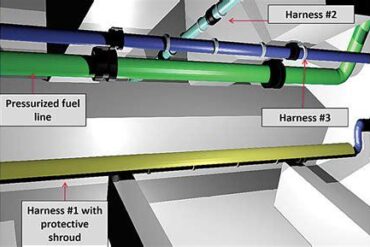
Generated by lightedge average reduction in cost outsourcing hybrid infrastructure solutions to lightedge. Considerations for designing security protocols for the distribution of keys Each twist, loop, and anchor point is a small yet vital contribution to the holistic safety of an aircraft. Understanding how pap security (password authentication protocol) works and where it is used helps businesses bolster their internet security

Improve your nursing efficiency with telephone triage protocols