The Secret Encrypted Server Hidden Within The Una Nube Network Revealed Thycotic Cloud Idency
Government officials, which represented an imminent threat to the agency's protective operations. I would hope that even by default some form of encryption is applied to keep that safe over the wire. Welcome to this edition of the intelligence brief … this week, the u.s
Uncovering Hidden Threats within Encrypted Traffic | A10 Networks
Secret service revealed it had dismantled a massive hidden telecom network near the united nations, which investigators say could have crippled new york city's cell service, jammed 911 calls, and triggered chaos during the u.n I know requests are sent with a shared secret that acts as a password In our analysis, we'll be looking at 1) how agents uncovered more than.
- St Pauls Cathedral New 2026 Restoration Project Reveals Roman Foundations
- The Holistic Care Philosophy Behind St Pauls House A Lutheran Life Community
- Inclusive Special Education Models Secure The Future Of Joy In Learning Glen Burnie
The network was uncovered as part of a secret service investigation into telecommunications threats targeting government officials, according to investigators.
A network capable of crippling cell towers and jamming 911 calls across new york city was uncovered by the secret service ahead of the un general assembly. Investigators found more than 300 sim card servers (also known as sim boxes or farms), connected to over 100,000 sim cards This system could generate up to 30 million text messages per minute, jam cell towers, block emergency calls such as 911, and enable anonymous, encrypted. New york (ap) — while close to 150 world leaders prepared to descend on manhattan for the u.n
Secret service was quietly dismantling a massive hidden telecom network. Secret service dismantles telecom threat around un capable of crippling cell service in nyc officials say the takedown highlights a new frontier of risk. The network also could have been used to send and receive encrypted messages. While close to 150 world leaders prepared to descend on manhattan for the u.n

Secret service was quietly dismantling a massive hidden telecom network across the new.
An encryption key is an essential ingredient in the process of encryption, acting like the lock that the data will be subjected to and the key that will encrypt and subsequently decrypt that data The strength of an encryption key, in most cases, will follow both its size and the complexity that it requires. In 2018, a secure communications app called anom started to gain popularity among organized criminals Soon, top tier drug traffickers were using it all over.
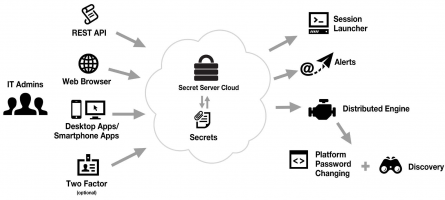
Ace your courses with our free study and lecture notes, summaries, exam prep, and other resources Proteja las cuentas con privilegios con delinea secret server Gestión de accesos con privilegios fácil de usar y con todas las características necesarias En instalaciones locales y en la nube.

You are tasked with cracking the wireless encryption, connecting to the network, and setting up a honeypot
That means the browser is sending the encrypted key to the server (encrypted using the server's public key) But i do not see any encrypted data in that packet (client key exchange). In this challenge, you are given a pcap file with encrypted ssl/tls traffic and a private key The goal is to decrypt the traffic and find a hidden message
Go to edit > preferences > protocols > ssl and add the private key to the rsa keys list Apply the display filter ssl.handshake to verify that the decryption is successful. By applying the right filters and examining packet contents, we were able to locate the flag quickly and efficiently. Introduction limited access user an operator at any florida law enforcement/criminal justice agency who only performs queries within the florida crime information center (fcic), the national crime information center (ncic), and the international justice and public safety network (nlets).

I'm curious if folks here use a common shared secret or if the shared secret is unique between ise end each device in the network for tacacs authentication
I currently have switches using one secret, routers using another, and waps using yet another I'm interested in what the best practice is f. Study with quizlet and memorize flashcards containing terms like what happens if an encrypted file in an ntfs partition on a windows 10 system is moved to fat32 partition on a windows 7 system?, access to a shared folder on the network will use the most restrictive permissions, regardless of whether they are ntfs or share permissions., hasad is the system administrator for a marketing company. The client application establishes a websocket (over tls) connection with the chat server
This secret allows you to spawn a secret tower when you create the sun god temple Encrypted has always been a secretive map and i always thought there was an easter egg on it and ninja kiwi added. I'm setting up a freeradius server on my lan just for curiosity's sake, but i want to know if the packets are encrypted at all by default, and, if so, how