The New Scan Com Login Update Features Instant Zero-trust Authentication Zero Trust Auntication And Least Privilege
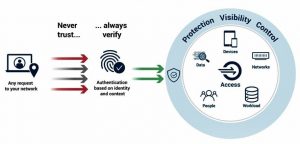
Learn best practices to authenticate app users and enhance application security with zero trust principles of least privilege and verify explicitly. Manage identities and access for apps, data, and resources with microsoft entra admin center, a comprehensive solution for secure identity and access management. Strengthening security with continuous authentication we are excited to introduce zero trust continuous authentication (ca) in the yokohama release—an advanced security capability that continuously verifies user identity beyond the initial login
ZeTA: Zero-Trust Authentication | Download Scientific Diagram
This feature aligns with zero trust security principl. This configuration means that authentication requests can be passed between the two domains in both directions. What are the pitfalls of traditional security measures and why are they no longer reliable in today's digital landscape.
- Aa County Youth Basketball New Aacrp Initiatives Reshape 2026 Player Development
- Year Round Learning Modules Reshape The Glen Burnie High School Calendar
- New Data Reveals Saint Pauls School Alumni Dominate 2026 Tech Unicorn Leadership
Protect against credential theft, deepfakes, and 85% of ransomware attacks
Explore how continuous authentication in zero trust revolutionizes cybersecurity, enhancing protection and user experience across industries. Zero trust authentication is a strict it security model that limits permissions and requires proper authentication from every user accessing company resources, whether they are part of or outside of the network. Through the zero trust access controller, admins can manage the current ivanti secure access client (isac) version for end users. This article helps you, as a developer, to understand identity and access management best practices for your application development lifecycle
You start developing secure, zero trust compliant applications with identity and access management (iam) The zero trust security framework uses the principles of explicit verification, least privileged access, and assuming breach The okta and auth0 platforms enable secure access, authentication, and automation — putting identity at the heart of business security and growth. Sectigo is a leading provider of ssl certificates & automated certificate management solutions
A certificate authority trusted by global brands for 20+ years.
Identity verification app protection at login Explore our comprehensive cybersecurity glossary, featuring clear definitions of key terms, concepts, and jargon Stay informed and enhance your cybersecurity knowledge with expert explanations. Looking for the best prop firm
Funding pips empowering your success on all major trading platforms like ctrader, match trader, tradlocker etc. Cloudflare access is a fast, reliable zero trust network access solution that secures employees and contractors This question is for testing whether you are a human visitor and to prevent automated spam submission What code is in the image

Submit your support id is
Where the world charts, chats, and trades markets Guaranty trust bank ltd is a leading african bank that offers online/internet banking, retail banking, corporate banking, investment banking and asset… Built for zero trust and powered by ai, the strata™ network security platform proactively monitors, analyzes and prevents sophisticated threats in real time with less complexity, enabling secure growth and innovation for your organization. Hdfc bank, india's leading private sector bank, offers online netbanking & personal banking services like accounts & deposits, cards, loans, & investment.
Explore enbd x application, the innovative mobile banking app in the uae by emirates nbd Enjoy seamless banking experiences, advanced features, and personalized solutions