Loguin: The 2026 Cybersecurity Protocol For Secure Enterprise Access Imprivata Vendor Privileged Management Merly Link
As organizations continue migrating to the cloud, cybersecurity strategies must adapt in parallel Cybersecurity stocks are shares of publicly traded companies whose primary business is protecting digital assets and networks—covering areas like endpoint and network protection, identity and access management, encryption, cloud security, and security consulting. This shift is not just about securing environments.
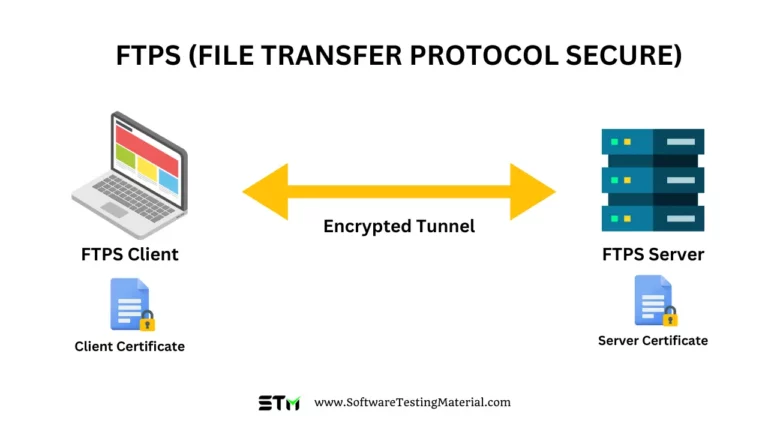
What is SCP (Secure Copy Protocol)
The global cybersecurity outlook 2026, written in collaboration with accenture, examines the cybersecurity trends that will affect economies and societies in the year to come It's also true that ai. It explores how accelerating ai adoption, geopolitical fragmentation and widening cyber inequity are reshaping the global risk landscape
- Why The Sgb Weekly 2026 Digital Edition Surpassed Print Sales
- Altar Designs Revolutionized 2026 Trends Embrace Sustainable Materials
- Inside The Inclusive Coaching Strategies Of Hershey Coed Soccer
As attacks grow faster, more complex and more unevenly distributed, organizations.
With enterprises expected to deploy a massive wave of ai agents in 2026, the cyber gap narrative will fundamentally change The widespread enterprise adoption of these agents will finally provide the force multiplier security teams have desperately needed. What will enterprise cybersecurity hold for business in 2026 and what will cybersecurity leaders need to do to protect their firms from new threats? Industry experts outline the risks that will shape business cybersecurity in 2026, and how organizations are preparing
The era of prevent everything is over In 2026, cybersecurity experts predict the sector will no longer be a technical problem to be contained, but a business risk to be managed. How do we secure a modern, distributed enterprise when assets, identities, data flows, and execution logic no longer reside within clearly defined, manageable boundaries? What you need to know about age restrictions, data leaks, safe ai, and other cybersecurity trends that will shape the year 2026.
The cert division is a leader in cybersecurity
We partner with government, industry, law enforcement, and academia to improve the security and resilience of computer systems and networks We study problems that have widespread cybersecurity implications and develop advanced methods and tools to. Includes beginner paths, key skills, certs, and next steps. The essential network security checklist for 2026 1
Implement strong access control measures controlling who can access your network and its resources is foundational Weak access controls are a common entry point for attackers Principle of least privilege (polp) Grant users only the minimum access necessary to perform their job functions.
Expert insights on external attack surface management (easm), the process of finding and managing every asset exposed to the internet.
Cloq) is a cybersecurity company focused on fraud prevention and secure access solutions Cyberheistnews vol 16 #01 | january 6th, 2026 ai & cybersecurity in 2026 Top 10 predictions for threats and defenses as we head into 2026, artificial intelligence looms as both innovator and instigator in cybersecurity Get the most complete identity security and access management solutions that enable secure access across any device, anywhere, at just the right time.
As a leader in vulnerability management, tenable helps you know, expose and close cyber risk using robust cloud security and exposure management tools. Taking a big picture view of the high cybersecurity world entering 2026, it's clear generative ai will be used much more widely to launch and prevent cyberattacks